§2024-10-01
DKIM (DomainKeys Identified Mail) is an email authentication method that allows a mail server to verify that the email message's content has not been altered in transit and that the sender's domain is authentic. It provides a way to associate a domain name with the email message, which helps prevent email spoofing.
- Key Concepts:
-
Public/Private Key Pair:
- The private key is stored securely on the mail server and is used to generate a digital signature for each outgoing email.
- The public key is published in the DNS records of the domain, so that receiving servers can verify the signature.
-
Digital Signature:
- When an email is sent, the mail server uses the private key to generate a cryptographic signature that is attached to the email's header in a field called DKIM-Signature.
-
DNS Records:
- The domain's public key is stored in the DNS under a TXT record. The receiving mail server fetches this public key to verify the email’s authenticity.
-
Verification Process:
- The receiving mail server extracts the DKIM signature from the email and retrieves the public key from the DNS.
- The public key is used to verify that the email was signed with the corresponding private key and that the content was not tampered with.
-
Steps to Set Up DKIM on a Mail Server:
- Generate a Key Pair:
- Generate a public and private key pair on your mail server. The private key will be stored on the mail server, and the public key will be published in your DNS records.
- Generate a Key Pair:
2.1. Using openssl to generate privae.key and public.key
alexlai@mail:~/build/tmp$ pwd
/home/alexlai/build/tmp
alexlai@mail:~/build/tmp$ openssl genpkey -algorithm RSA -out private.key -pkeyopt rsa_keygen_bits:2048
.....+.+...+...+.....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+.+..+.+.....+......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*......................+..+............+.+..+..........+...+..............+.+..+.+......+...+........+.......+.....+......+....+...+...+......+......+........+....+.....+..........+......+.........+..+.+.....+.......+.....+.+...............+.....+.+......+....................+..........+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
...+..........+.....+...+.+..............+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+..+......+.......+..+.+.....................+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+....+..+.........................+...+..+.+............+..+.........+......+...+.+..+.............+.........+......+.....+....+.....+.+.....+.+......+.........+...+..+.+..+.......+...........+..........+..+.+......+.....+....+..............+.+...........+....+......+........+.+.....+......+......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
alexlai@mail:~/build/tmp$ ls
private.key
alexlai@mail:~/build/tmp$ openssl rsa -pubout -in private.key -out public.key
writing RSA key
alexlai@mail:~/build/tmp$ ls
private.key public.key
alexlai@mail:~/build/tmp$ cat private.key
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDFW0fGhlHQnnl2
yUiRhZw3oNFoIhjgTGwf7XRtVat0E/P+3XdqzRDmEUY2ctCJBkSzTaHUmkDoDGHd
z9k+sej/EefEbqz/jEcf0mnKwA/6tTRfjTKK5ik48OSied4gJ9ZKOtV2mHZ7UNMy
64c2G6wXMZhS71MkfGRyBalkYBbgxUHS/GrgUidoLYLGmNtaz3JwPzFL0mrgKuMH
1gQzFA7lK3nQuyhlKGScEQu6YfO29Uskr/QM0fucznXE9QQyh/vuKU9ciO4L/69V
qcoC5EL4eEi0pTmojFc7piHa23lSn16tJ8ArFd2mSzrkaWxDVNbfZz+2ja8OzCn8
c521yiwtAgMBAAECggEAKmqvdwIodGuTFI43XBt401Xrm/N0IEUcmhIZi2Q1yOl+
8ACeaWRwpNoCmrI7kq+3tUfSp9SNbbI3mIpTGU/4kVXCV+wnn3cBVFwPY8W6yXoH
qx+4RLUqF/RiV29U59lYC7UwauBi2qco9VE8ysrQxl1g7TZFyto3ZnBEE3A5io5J
/j94e1yHGb2P9iIjfLDcmSAaQysBVLtf7aHSVre+/LkmxH4ikIw1IY15FYn3UDGo
p3kIp7L3i0q8RIuH+E2FRCfFmMpsUydGu8uTPWKHAabRlWb14GnxR6DJhx6GYj9+
o5I1RsAcJg3S+sBBd7IrknNqjDgbvhP2KX8Em1fWiwKBgQDwHUS/QX3zimyU4f3r
5ujE+N/5Qx0EcXSIVg+C/cY+S2Bs8gda9iEzsu6PuoCcT+aaJlPNc6gjTSS0Y7sU
7wNEXxAuwznEuojCScNLW/zzTD5qzYOx0y+qzHn97xl8/chokdrP6lFGHTWilWF3
8uJScb6zzLxe20y/fnKe4AxmWwKBgQDSadazFY4aeKULqzCAhHFdFr4OfaPOmLgt
jF4HIxK79G/i1EWXBjyfGWn43mR03rYOWHwndRWcsYK+BX450cf9T3MYwV2uT3IA
rtcXTVoT1ElK+XNGgbdVqrh94zJOLSFQ8VQsv5DgquYfOjUo9UxyCtxfLH9yKpRN
r6BuaXwOFwKBgQCvqSnnJXmIVwdysBY8o7Q8jboFOBUdcAcJyrQUZ6XFYw2LBlFd
OV023jtqyM1YDZgtw8ZhMrCaCtDEa4WtHeJs/YLwQwCbLL/qK16FXimisG+lYO5s
hIyFzoucu3QRHfSkk7fZjZmhyrK3W8Nvpi/ukqoqDajtWFBAc7hVBKHtqwKBgQCX
N18IJvaQSaH7h9T8l7JM/zopedvObuz2NwmgQXGGSH5cWseEaQQKJx6Er3cskp3u
I2NejAOzL9NRMutrLDt47a8+3ECyNAAvQ3frFDknRQpDapCQ3Epgs6eROUV+72oh
HL6sxiOdgtSNHqzzuY5t6yZC89zHtJgOWKiIkSCJkwKBgHyJ6Ir3k88149TnyB5l
1LCWWsx77RM9sgMexk+D8dhj8/wfLBhf1Fi7Ax+AeUBTOfpMU2qeZwdaAcnJD8QX
VN8j3BC/ydE6t0kB67FK4JFgC+taqzuf0vEeI1e+ncmm8hhzjm5A1fpeLVekZGSQ
/Nxu2cFTW4st7yRQar2E/9aj
-----END PRIVATE KEY-----
alexlai@mail:~/build/tmp$ cat public.key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAxVtHxoZR0J55dslIkYWc
N6DRaCIY4ExsH+10bVWrdBPz/t13as0Q5hFGNnLQiQZEs02h1JpA6Axh3c/ZPrHo
/xHnxG6s/4xHH9JpysAP+rU0X40yiuYpOPDkonneICfWSjrVdph2e1DTMuuHNhus
FzGYUu9TJHxkcgWpZGAW4MVB0vxq4FInaC2CxpjbWs9ycD8xS9Jq4CrjB9YEMxQO
5St50LsoZShknBELumHztvVLJK/0DNH7nM51xPUEMof77ilPXIjuC/+vVanKAuRC
+HhItKU5qIxXO6Yh2tt5Up9erSfAKxXdpks65GlsQ1TW32c/to2vDswp/HOdtcos
LQIDAQAB
-----END PUBLIC KEY-----
alexlai@mail:~/build/DKIM_DMARC$ cat public.key | sed '1d;$d' | tr -d '\n' | sed 's/.*/"v=DKIM1; k=rsa; p=&"/'
"v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmT0vFIGpAUrCnBPU24b7YxRONjRPYCnTHnKjwttSjbYF1vC0mAN64831E0QRGZwX+8wzbkXHSqusVtNf5/dj/HmfvoHMtfh+NTI3utpTbIsYbdaiDzRhLEhzXC0hW/8hNayDrJ0XOjFmvO9tS9Km480YxO4aszWfw2eIOKZIRPSBf2Ii2SlsvXZh64wrT3T7x6i3MX25Z630zbHAapK0J+D2uC8XAwtKoG12rkJ0NdxrM3h1BzCsOKT6pCCpMamWicFdimD04RnW2P+hj7xUCm5ElKcJnCrkJTV+sHMqM0tRMnMG5j4PRgaNsjC+rebAEIgXLMx7FoP9KsmWj9oF1wIDAQAB"
- Configure the Mail Server:
Configure your mail server to sign outgoing emails with the private key. This often involves configuring the MTA (Mail Transfer Agent) such as Postfix, Exim, or others, to use DKIM.
- Publish the Public Key in DNS:
-
Add a TXT record to your domain's DNS records containing the public key. The DNS record should look like this:
-
the keys are in yushei.net:/home/alexlai/build/DKIM_DMARC/
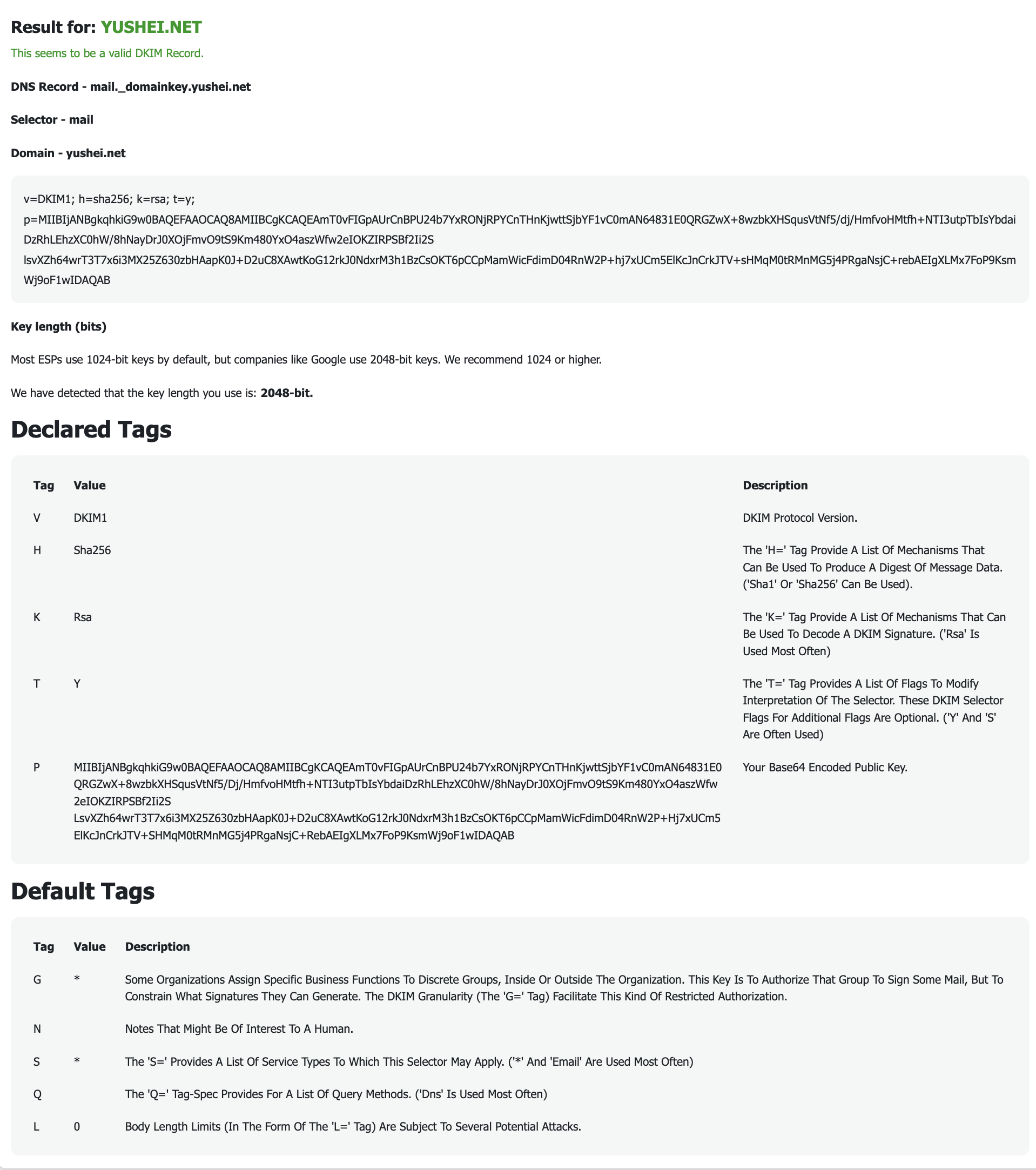
DNS Record - mail._domainkey.yushei.net
Selector - mail
Domain - yushei.net
v=DKIM1; h=sha256; k=rsa; t=y; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAmT0vFIGpAUrCnBPU24b7YxRONjRPYCnTHnKjwttSjbYF1vC0mAN64831E0QRGZwX+8wzbkXHSqusVtNf5/dj/HmfvoHMtfh+NTI3utpTbIsYbdaiDzRhLEhzXC0hW/8hNayDrJ0XOjFmvO9tS9Km480YxO4aszWfw2eIOKZIRPSBf2Ii2S lsvXZh64wrT3T7x6i3MX25Z630zbHAapK0J+D2uC8XAwtKoG12rkJ0NdxrM3h1BzCsOKT6pCCpMamWicFdimD04RnW2P+hj7xUCm5ElKcJnCrkJTV+sHMqM0tRMnMG5j4PRgaNsjC+rebAEIgXLMx7FoP9KsmWj9oF1wIDAQAB
default._domainkey.example.com IN TXT "v=DKIM1; k=rsa; p=PUBLICKEYHERE" The default selector can be customized depending on how you want to manage DKIM keys for different parts of your domain. Test the Setup:
Send an email to a service that checks for DKIM, such as mail-tester.com, to verify that the DKIM signature is working properly. Example DKIM Workflow: Sender: An email is sent from user@example.com. The mail server for example.com generates a DKIM signature using its private key and adds it to the email. Receiver: The recipient's mail server checks the DKIM-Signature in the email header, retrieves the public key from the DNS of example.com, and verifies the signature to ensure the email's integrity and authenticity. Benefits of DKIM: Prevents Email Spoofing: Ensures the email truly comes from the domain it claims to. Improves Deliverability: Some mail providers use DKIM to score your domain's reputation. Part of DMARC Policy: DKIM is often used in combination with SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance) to fully protect against spoofing. Would you like more detailed instructions on setting it up for a specific mail server (e.g., Postfix, Exim)?